Authentication Methods
Supported Types of Authentication
Castle supports the following step-up challenges that allows your organization the flexibility to implement the authentication methods that fit your unique requirements.
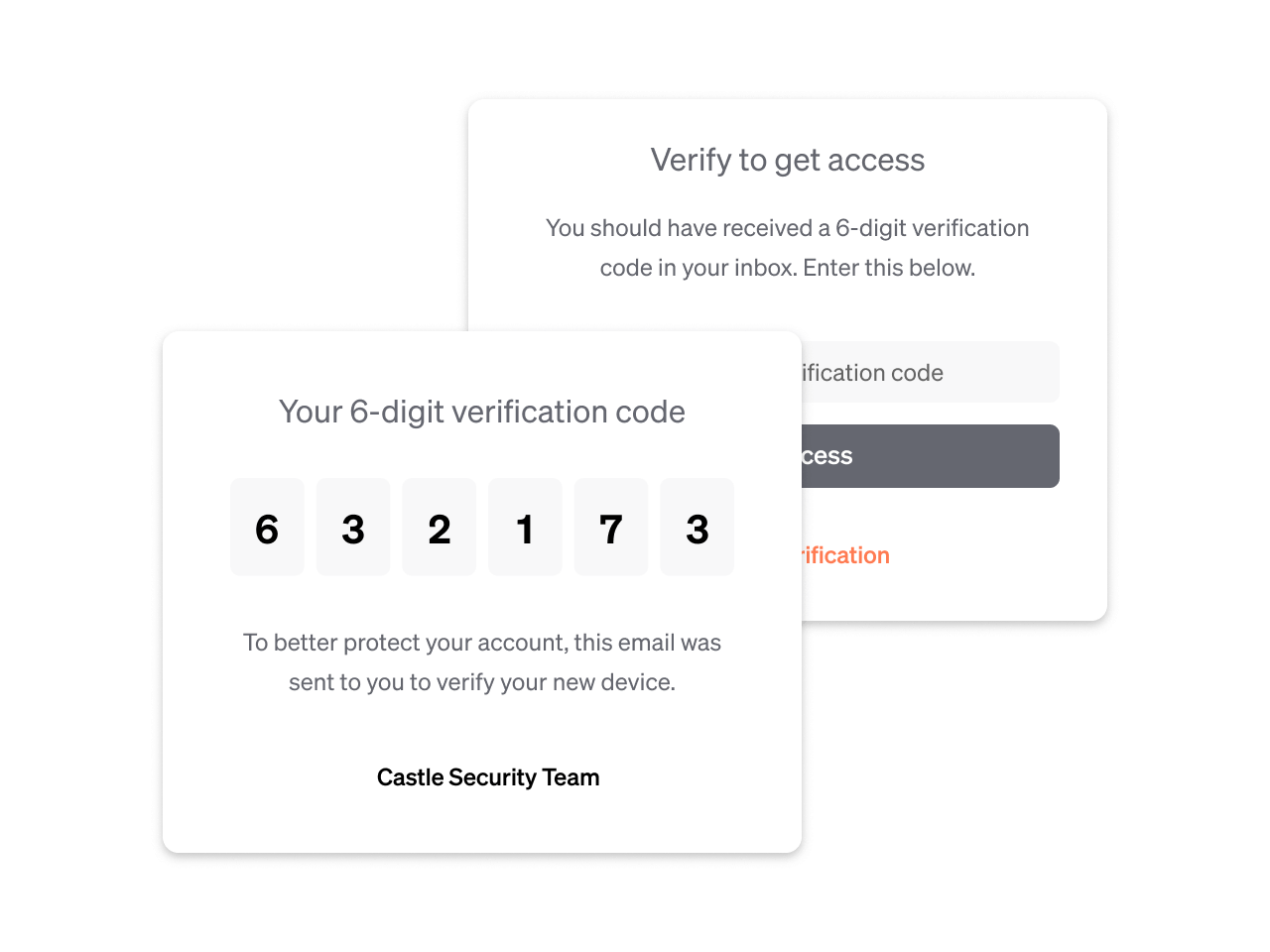
SMS
Voice Call
Email Verification
Pin Code
Push Notification
Risk Tolerance
Adaptive Remediation Means Less Friction
With Castle, you can easily automate intrusion alerts, step-up authentication, and account recovery workflows, but only appropriate to the specific level of risk. You can deny the riskiest logins and in-app transactions (such as profile changes or abnormal transactions) outright while still ensuring legitimate users can use your application without any friction.
Read Our Datasheet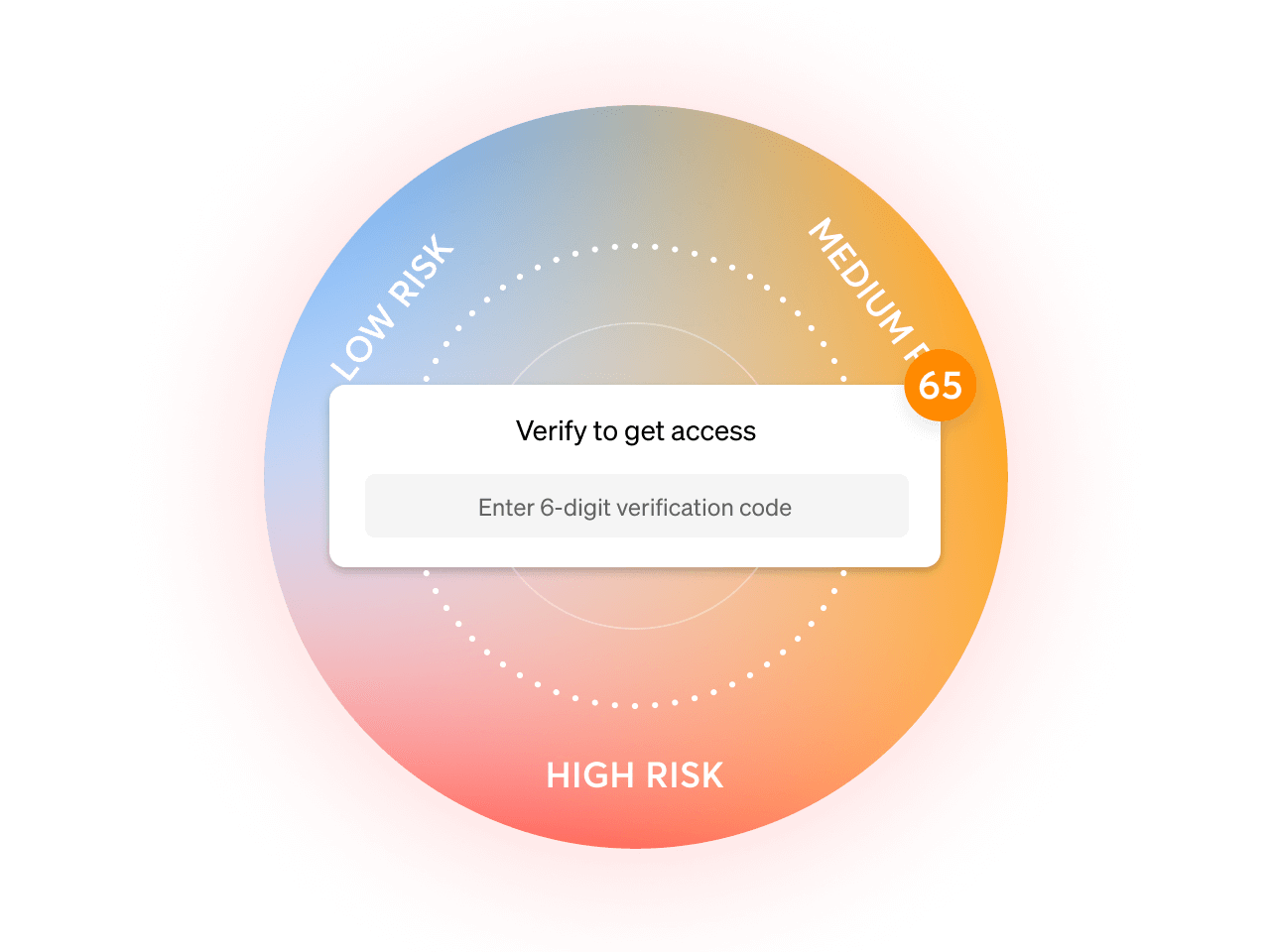
Risk Policies
Build A Custom User Journey
Leverage Castle’s granular risk policies with customized logic, risk scores, and responses to implement custom segmented user journeys based on risk tolerance. Build custom policies that meet your unique business requirements - protecting users, their devices, and their activity with your application.
Read Our Datasheet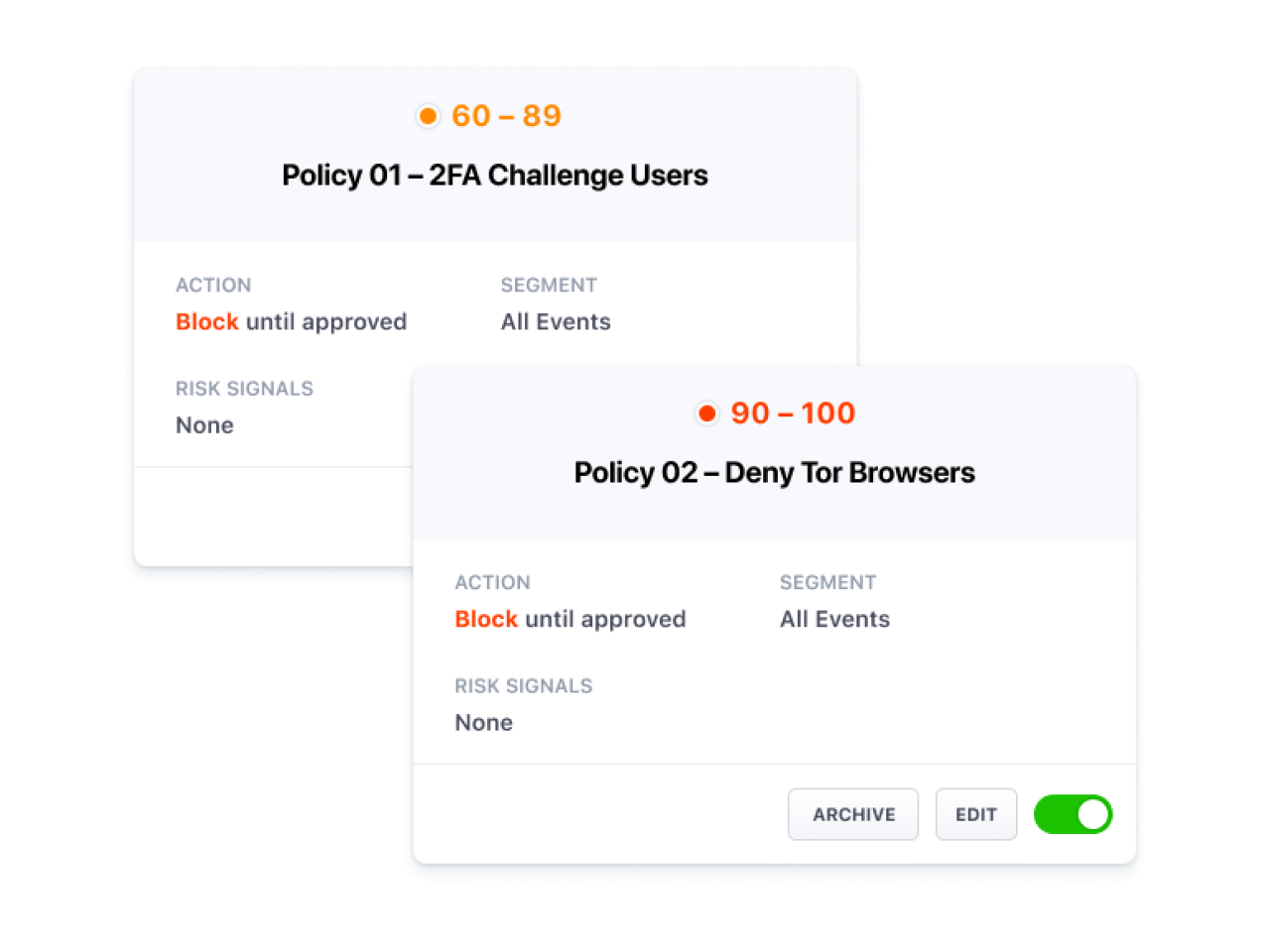
INFOGRAPHIC
Stopping Account Takeover Attacks
Learn more about the anatomy of an Account Takeover attack that compromise user credentials and what you can do to defend yourself.
Download Infographic
